Information Assurance
CORE-CSI understands today's dynamic threats to our customers. Our computer security professionals are well-versed in security best practices as mandated by various Federal Mandates. We follow industry standards and best practices, Department of Defense and Intelligence Community Standards, and National Institute of Standards and Technology to mitigate and defend from Advanced Persistent Threats (APTs). We provide advanced Computer Network Operations (CNO) and Computer Network Defense (CND) and Information Assurance (IA) services in support of our customers' missions. CORE-CSI incorporates the NIST-based Risk Management Framework (RMF) to track, prioritize, and mitigate vulnerabilities.
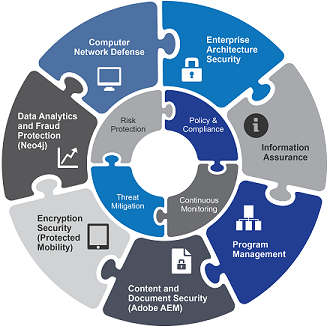
Our cybersecurity professionals and solutions help secure information, infrastructure, and personnel from threats and attacks to prevent the loss of valuable data and resources. CORE-CSI offers cleared, experienced, certified, and skilled security professionals with expertise across a wide range of programs, and information security engineering services.
Information Assurance Services
- Preparation of A&A packages for varied Impact levels system (HHH – MMM – LLL)
- Development of security classification guides based on CAPCO and Concepts of Operations (CONOPS).
- Preparation of System Security Plans (SSPs) and System Security Authorization Agreements (SSAAs).
- Development of security inspections and patch management processes, assessments, and recommendation of mitigation strategies.
Operational Security
As one of the world's leading cybersecurity service providers, we are best placed to help businesses identify, assess, mitigate & respond to the cybersecurity risks they face. Through an unrivaled suite of services, we provide our customers with peace of mind that their most valuable assets are protected.
OPERATIONAL SERVICES
Security and Privacy Assessment
- NIST Security and Risk Standards
- ISO Security and Risk Standards
- HIPAA/HITECH
Security Build Services
- Incident Response Program
- Policy Development
- Security Architecture Framework & Design
Security and Data Privacy Consulting
- Chief Information Officer as a Service (CISO)
- Information Security Expert as a Service (ISE)
- Data Privacy Expert as a Service (PDE)
Privacy Build Services
- Incident Response Program
- Policy Development
- Security Architecture Framework & Design
Ethical Hacking - Technical Assessments
- Vulnerability Assessment
- Network Penetration Testing
- Web Application Security Assessment
- Wireless Network Security Assessment
- Social Engineering / Phishing Simulation
- Physical Security and Penetration Testing
Threat Hunting Service
- Review and Correlation of your system
- Staff training
- Help staff design, implement and deploy a log monitoring platform
- Create/fine tune custom notifications for malicious activities
AREAs OF SUPPORT
- Cyber Security and Intelligence
- Imagery intelligence (IMINT) Systems
- Financial Management and Budgeting Systems
- Assessment and Authorization (A&A)
- Vulnerability Management
- Human intelligence (HUMINT) Systems
- Health and Grants Management Systems
- Risk Management
- Operational Security (OPSEC)
- Vulnerability Assessments and Reporting
CUSTOMERS

United States Army

